Mid-2012. A Tiny malware was discovered in Turkey. This little malware attacked thousands of computers in Turkey. How did this tiny little mutant work? It identified when user browses through a banking site on an infected computer and asked user to enter sensitive information. The user, believing the form presented on the screen was authentic and published by the bank itself, enters the information like credit card number, expiration date, CVV and pin. That’s it. The user has given away his most sensitive financial information to someone unknown.
Known as Tiny Banker, this malware is actually tiny, with about only 20 KB in size. But its size does not give idea about how powerful it is. Tiny Banker is hooked into user’s web browser and sniffs the network data. Even without any packing or advanced encryption, its detection ratio by antivirus is low. The source of Tiny Banker is fake email. According to Avast analysis, the attackers attempt to scare their victims with a specially designed email message explaining that a debt exists which needs to be paid. This email contains a .zip attachment. This zip file contains an executable file. This executable file is actually a downloader which downloads and executes the infection in user’s computer.
Now Tiny Banker also known as Tinba has striked again. This time, US based banks are prime target for Tiny Banker. A version analyzed by Avast showed Tiny Banker has been customized to target many new financial institutions, including US based banks such as Wells Fargo, Bank of America and Chase, according to Jaromir Horejsi, an Avast malware analyst.
The malware tricks users into entering the information by showing a fake warning of system update. This fake warning appears only when user visits the targeted bank’s website, making user believe that the warning might be authentic.
The process of this tiny but sophisticated attack is described by Avast to be as below:
1. The user visits a website infected with the Rig Exploit kit (Flash or Silverlight exploit).
2. If the user’s system is vulnerable, the exploit executes a malicious code that downloads and executes the malware payload, Tinba Trojan.
3. When the computer is infected and the user tries to log in to one of the targeted banks, webinjects come into effect and the victim is asked to fill out a form with his/her personal data.
4. If he/she confirms the form, the data is sent to the attackers. This includes credit card information, address, social security number, etc. An interesting field is “Mother’s Maiden Name”, which is often used as a security question to reset a password.
Below are some screenshots which show fake system update warning while visiting a bank’s website.
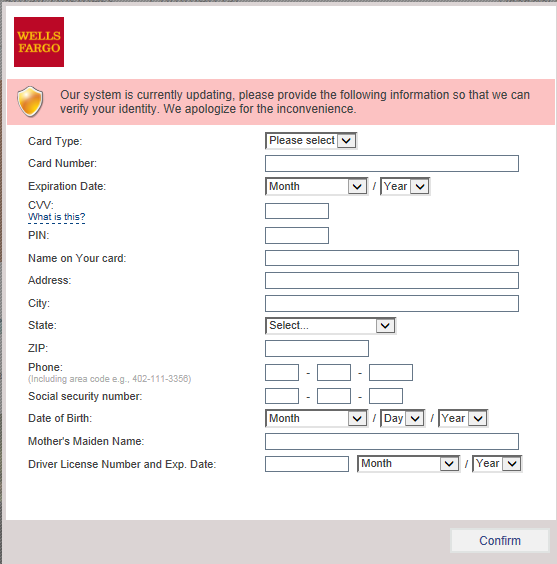
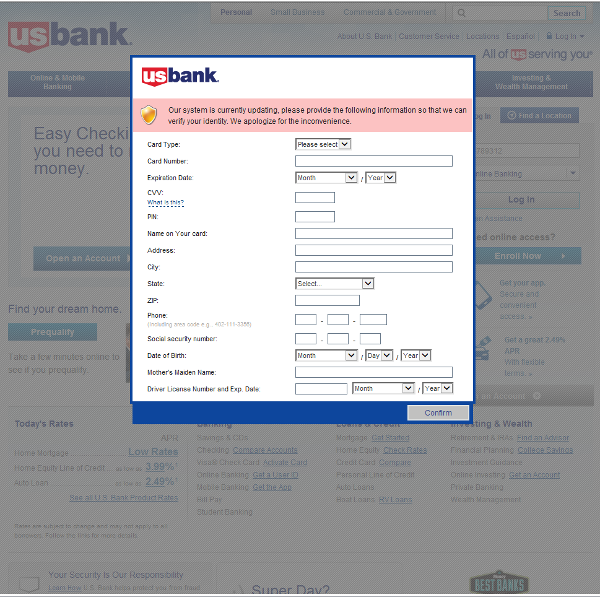
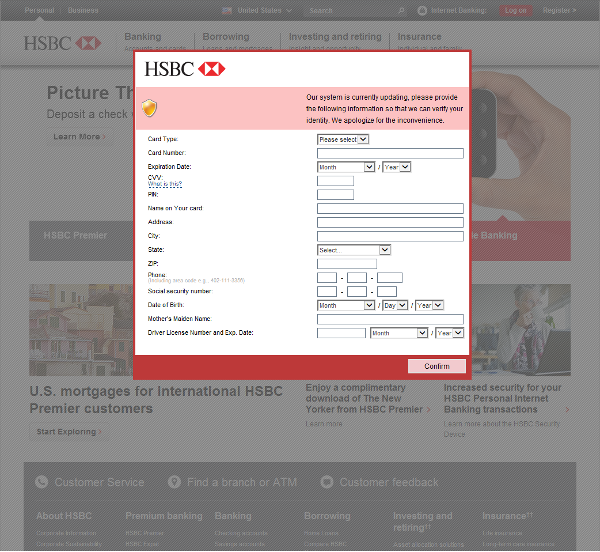
How to stay safe online? How to avoid being a victim of malwares such as Tiny Banker?
Do not open emails came from unknown sources unless really important. Most of the time, the title of email itself tells you the whole story. Look for typos, mistakes in email titles. Look for ALL CAPS. If any of this is there, it is probably a fake mail and you should delete it right away.
If you open such email because you were expecting one, take a look at the sender first. And by sender, I mean the email ID, NOT the name (any one can email using any name they want). If the sender’s email ID is not on the same domain as the expected sender, it is probably a rouge email.
Look at the email’s content carefully. If you see typos, spelling mistakes, unusual capitalization or unprofessional language, you should stay away from the email. No bank or any other reputed institution will ever draft such mail to you.
Figure out the purpose of the mail. What does this email want from you? Does it want you to open the attachment? Does it want you to follow a link? If so? There are good chances of this email being dangerous. Either the attachment, or the link it wants you to follow is infected.
There are many other ways of identifying and dodging such attacks. But the best thing to do is to use common sense. I mean, why would a bank ever call you or email you to get your credit card number or password? What will the call be like? “Hi, I am calling from XYZ bank. Our database recently crashed. And we are calling/emailing everyone to get their details back!” Nothing about this conversation makes sense.
That’s all in Tech Stuffer’s weekly security post. We will be back with more articles. Be safe. Do not blind trust anything while you are online.
How did you find our article? Have something to say about Tech Stuffer? Want to give feedback/suggestion on how to improve? Feel free to contact us anytime.Credit: Avast, the Internet
Support Me: If this article/tutorial helped you today, please consider supporting me and help me run frunction.com