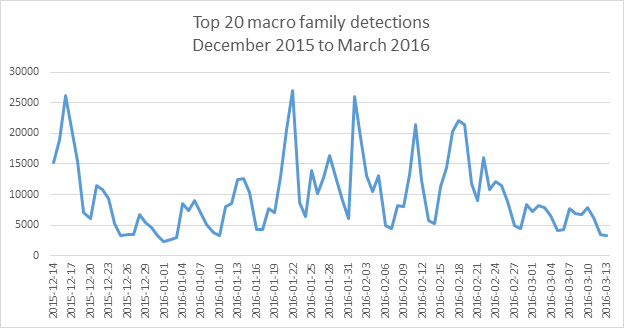
Macros are one of the most popular medium for malicious users to spread malware. Macro-based malware is usually spread via emails and other means of communication.
These emails typically use attention-grabbing titles and message to lure users into opening attachments and eventually infecting his/her device.
Microsoft Office is one of the prime victims of Macro-based malware. Microsoft also acknowledge that macro-based malware is on the rise as recent data from Microsoft’s Office 365 Advanced Threat Protection service suggests that 98% of Office-targeted threats use macros.
Although Microsoft Office applications display a warning prior to opening a macro, strong social engineering tactics used by attackers end up convincing users into enabling macros.
Fighting Macro-based Malware with Office 2016
To fight macro malware, Microsoft is introducing a new security feature in Office 2016 which blocks macros from loading in certain ‘high-risk scenarios.’ This tactical feature in Office 2016 can help enterprise administrators prevent the risk from macros. This feature allows an administrator to selectively scope macro use to a set of trusted workflows and block easy access to enable macros in specific scenarios.
The new security feature will also provide end users with stricter notification making it easier for them to distinguish a high-risk situation against a normal workflow.
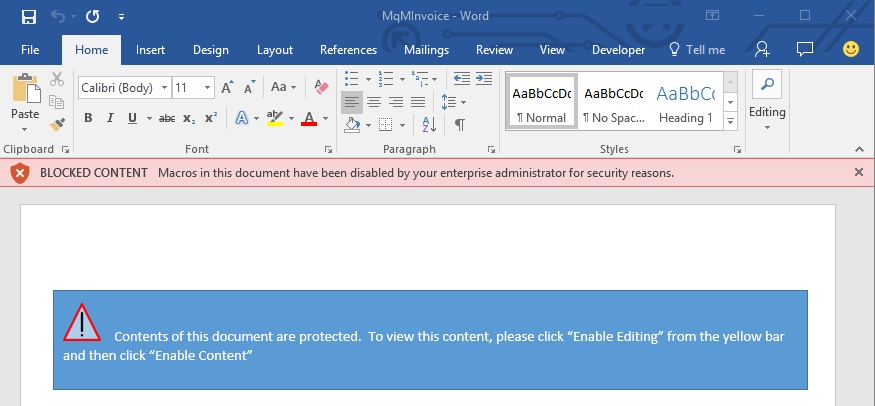
This feature can be controlled via Group Policy and configured per application. Administrators can block macros from running in Word, Excel and PowerPoint documents that come from the Internet.
Macro-based Malware: How to ensure protection?
To ensure maximum protection from malware spread via macros and other similar mediums, it is best to avoid opening attachments sent by unknown sources. Attackers usually have strong skills to convince you to open emails and attachments. If you’re unsure about particular attachments, you should always consult your IT department before opening suspicious emails and attachments.
Have you ever been victim of macro-based malware? Share your thoughts and experience with us.
Source: Microsoft
Support Me: If this article/tutorial helped you today, please consider supporting me and help me run frunction.com
