Okay, accept my apology for using such a cliché title but it’s extremely important that you update your WordPress sites right now. In fact, you should stop reading this, too and update your site before reading further.
A serious security vulnerability has been discovered in recent versions of WordPress that could leave your site open to hacking attempts. The latest version of WordPress (version 4.7.2) – which has been available now for about two weeks – fixes this vulnerability.
WordPress v4.7.2: Fixed Security Issues
According to its changelog, WordPress version 4.7.2 – the latest version of WordPress fixes four of the following security issues.
- The user interface for assigning taxonomy terms in Press This is shown to users who do not have permissions to use it.
- WP_Query is vulnerable to a SQL injection (SQLi) when passing unsafe data. WordPress core is not directly vulnerable to this issue, but we’ve added hardening to prevent plugins and themes from accidentally causing a vulnerability.
- A cross-site scripting (XSS) vulnerability was discovered in the posts list table.
- An unauthenticated privilege escalation vulnerability was discovered in a REST API endpoint.
All these security holes leave previous versions of update open to defacements. While the first three fixes were initially disclosed to the public, the last vulnerability – known as WordPress REST API Vulnerability wasn’t disclosed until one week after the release of WordPress version 4.7.2.
The reason for this was to allow website owners enough time to update their software and to stop this security hole from being mass-exploited.
The Damage Continues
Although the WordPress developers waited for a week before making this security issue public, the damage has already been done – and continues to be done.
While most web hosts like SiteGround provide auto upgrade feature for WordPress installations, many site owners simply don’t use it for whatever reasons. It has been two weeks after the update was made available but there are a number of WordPress sites that has been defaced by malicious users by exploiting this security hole.
Hackers are leaving signs of hacking by editing the title of blog posts and replacing it with something like ‘hacked by NG689Skw.’ If you search this term on Google, you will see a large number of sites that contain this string in their titles.
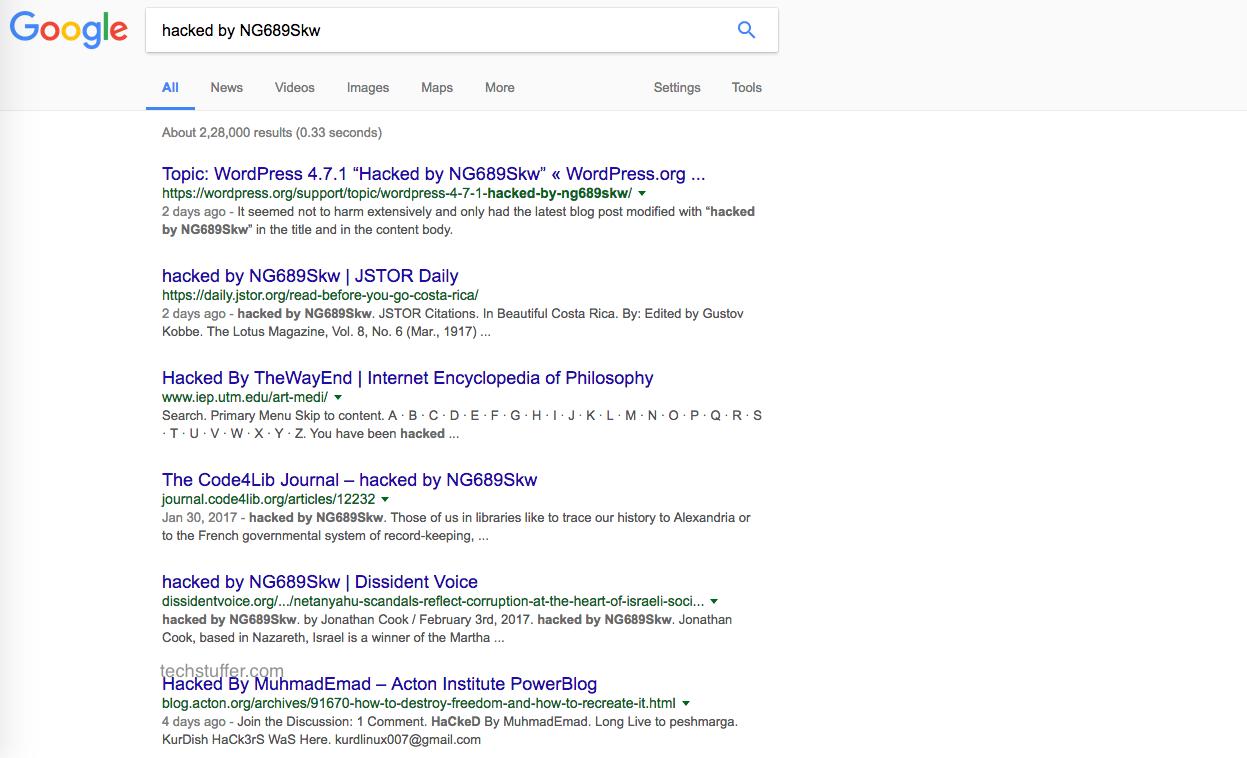
According to a blog post at Sucuri – the security firm that discovered the REST API Vulnerability – a large number of successful hacking attempts have taken place in less than 48 hours of this vulnerability being disclosed. Multiple public exploits have been created and shared online – making it easy for anyone to target a website running an outdated version of WordPress.
Is My Site Affected by This Vulnerability?
The WordPress REST API was recently added and enabled by default since version 4.7.0. If your WordPress site is running on version 4.7.0 or 4.7.1, then your site is vulnerable.
If you are running version 4.7.2, then this security hole has been patched on your site. This update could be applied either automatically by WordPress or your web host, or manually by yourself.
My Site Has Been Hacked. What Should I Do?
If your site shows any sign of being hacked, immediately follow these steps:
- Take complete backup of your site.
- Update your site(s) to WordPress version 4.7.2.
- Install a ‘Coming Soon’ plugin and take your site offline for a while.
- Look for any blog posts for terms like ‘hacked by’ followed by unfamiliar text strings (like w4l3XzY3).
- Edit these blog posts to remove any defacement
- Search your own site address on Google to identify any recent changes. (Not the best way, I know. but it could help.)
- After you are sure that you have removed every sign of defacement, deactivate coming soon plugin and bring your site online again.
How to Avoid Such Attacks in Future?
Most web hosts can automatically update WordPress installations on their servers. They will send you an email when a new version is available. If you had turned this feature off for whatever reason, or you are unsure whether you have turned it on or not, you should contact your host right away.
Don’t use cheap web hosts that don’t pay attention to its users’ security. This ‘cheap’ hosting comes at a cost. Insist on hosting your sites with well-known hosting providers like SiteGround who take your security seriously.
Always keep a fresh backup of your site. You should better be safe than sorry. You can use plugins like UpdraftPlus (free) to backup your WordPress sites.
Refrain from installing rogue themes and plugins downloaded from untrusted sources. Remove plugins you no longer use. Make sure your themes and plugins are always up to date along with your WordPress installation.
Update Your WordPress Sites: Summing Up
Long story short, if you haven’t updated your WordPress sites, log in to your WordPress dashboard, and click the update button right now.
If your site has been hacked, make sure you remove every sign of defacement before bringing your site online again. Your visitors will surely not like to see a defaced page and it could damage your brand and trust.
That’s it, folks, this was Parvez and you were reading ‘Stop Everything and Update Your WordPress Sites Right Away’ on techstuffer.com. I hope you found this blog post worth your time.
Share this blog post with your friends and advise them to update their sites immediately.
Sources: Sucuri, Sucuri, WordPress, WordPress
Support Me: If this article/tutorial helped you today, please consider supporting me and help me run frunction.com
